There’s a slight pre-req here, that may not be configured in production environments.
- It does require IE being allowed to browse to local paths from the address bar – this may be locked down through Group Policy
Consider something goes wrong and, to diagnose the users scenario further, one wants to interrogate and alter the users environment without getting changes caught in the wrong bubble – there’s an ‘easy’ way to break out of the virtual environment below.
Start with launching an IE-based published shortcut (that is presumably part of a bubble). Of course, if you’ve got a file-open dialog, it ought to work too, so any notepad-like tool ought to suffice. Get creative, you’ll be rewarded later.
Change the address to the C:\ of the server:
Explorer.exe is now a child-process of the published app. Navigate to System32 and double-click on CMD.EXE to run it on the server(this is a remote process):
Close the existing IE window down – This is important as we don’t want the OS re-using the process in a moments time. So we’ve got a console, but we’re still ‘in’ the bubble.
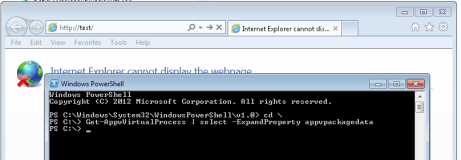
If you traverse to Powershell.exe you can confirm as below:
Execute ‘start-process http://test‘ in PoSH (or ‘start http://test‘ in CMD) and you’ve broken ‘out’ of the bubble – this is the ‘hook’ that breaks outside App-V’s virtualisation environment.
- Doesn’t need to be a real URL of course, we just want an IE window.
- Using ‘about:blank’ doesn’t work either – colon’s are reserved…
Because you are launching the http:// protocolhandler, it bypasses the usual mechanisms and (somehow) steps outside of the bubble – this OS function appears to be ‘beneath’ the App-V ‘stack’.
- If you want an IE within the bubble, properly pass the executable path ‘”C:\Program Files (x86)\Internet Explorer\iexplore.exe” {URL}’.
- This works on App-V 5 SP1 and SP3
Now you’ve got a console, external to any virtual environment. Close down the other processes (explorer.exe window and cmd.exe) to let the virtual environment shut down gracefully. Citrix will keep your session open just fine.
Repeat the browse loophole to re-launch another Powershell session (this time outside the bubble) if you wish to prove the point:
Sure, it would’ve been easier to just publish CMD.EXE, but maybe that’s not a given in production. Maybe that’s not delivered to your user that’s just reported an issue, right?
It’s always useful to know how to subvert the environment for troubleshooting purposes…